Specifically, in the maritime industry, ships are relying more on systems that utilize automation, digitization, and integration than ever before.
As this kind of technology continues to develop, it is crucial to ensure cyber risk management onboard ships is at the forefront.
Why?
The overlap of operational technology (OT) and informational technology (IT) onboard ships and the Internet connection they rely on creates an opportunity for a cyber attack that shipowners need to address.
As a marine coatings provider to protect your assets, we supply the right coating for your needs. We engineer a range of MarineLINE® coatings with high chemical resistance to sulfuric acid to be used on your ships. APC sees first-hand the technological evolution the maritime industry is experiencing and the critical role we play in the maritime value chain.
In this article, you will learn about maritime cybersecurity and why risk management is crucial, some of the biggest security challenges shipowners face, common risks affecting the industry, and best practices from the IMO to mitigate the risk that you should keep in mind.
Let’s get started!
Chapters
Chapter 1
What is Maritime Cyber Risk and Maritime Cyber Risk Management?
Rapid developments in technology have brought on benefits to many industries, including the shipping industry.
With these improvements come increased usage of cyber technologies that are critical and essential to the management and operations of many systems and processes onboard. Not to mention, cyber technologies also keep the crew, cargo and the ship itself safe and secure.
Thanks to the integration of IT (informational technologies) and OT (operational technologies) onboard from these technologies, ships are connected through connectivity and networking to the Internet. While these technologies and systems provide efficiency gains for the maritime industry, they also present various risks to critical processes and systems that are directly linked to the operation of systems that are critical for shipping.
What is Maritime Cyber Risk?
Source: DNV GL, YouTube“Introduction to cybersecurity in Maritime and Offshore”
According to the International Maritime Organization (IMO), maritime cyber risk is defined as the following…
“Maritime cyber risk refers to a measure of the extent to which a technology asset could be threatened by a potential circumstance or event, which may result in shipping-related operational, safety or security failures as a consequence of information or systems being corrupted, lost or compromised.”
Source: Nettitude, CIA Triad + Safety https://blog.nettitude.com/the-new-imo-maritime-cyber-security-guidelines-nettitude
In fact, because this is such a pertinent issue in the maritime industry, the IMO released guidelines, “MSC-FAL.1/Circ.3, Guidelines on Maritime Cyber Risk Management” that provide high-level recommendations on marine cyber risk management to safeguard shipping from both current and emerging threats.
We’ll dive into those guidelines in more depth later on in the article...
What is Cyber Risk Management?
Cyber risk management includes the process of identifying, analyzing, assessing, and communicating a cyber-related risk. From there, the risk is either transferred or mitigated to an acceptable level while considering the costs and benefits of actions taken to the stakeholders.
IT systems usually are more mature when it comes to cybersecurity because it has established training, technology, and procedures available onshore thanks to an information security management system (ISMS). A security breach with IT systems can have financial and reputational impacts; however, it usually does not impact the vessel’s operation or the crew onboard. [source]
Conversely, OT is less mature with cybersecurity. In fact, an attack on a ship’s OT systems can not only jeopardize the vessel itself but the crew’s safety as well.
Here’s a chart that further details what makes up Information Technology (IT) and Operation Technology (OT).

Source: DNV - GL https://www.dnvgl.com/maritime/insights/topics/maritime-cyber-security/index.html
In conclusion, this kind of risk management’s overarching goal is to support safe and secure shipping, which is operationally resilient to cyber risks.
Chapter 2:
Biggest Maritime Cybersecurity Challenges
Cybersecurity threats exploit the connectivity and complexity of crucial IT and OT systems onboard ships, which can jeopardize the ship and the crew’s safety and the cargo.
Because of this, it’s clear that cybersecurity should be a crucial part of an organization’s risk management.
Cybersecurity threats can be malicious actions such as hacking or infection of systems with malware or blameless actions like lacking software maintenance onboard vessels, faulty user permissions, unauthorized access to systems, weak passwords, etc.
Regardless if malicious or benign, both above actions should be taken seriously as credible threats to vulnerabilities in IT or OT systems that can comprise an entire vessel and its crew.
As a reminder, the maritime OT systems include:
- Vessel Integrated Navigation System (VINS)
- Global Positioning System (GPS)
- Satellite Communications
- Radar systems and electronic charts
- Automatic Identification System
Whereas IT systems make up:
- Administration, accounts, crew lists, and more
- Permits to work
- Planned maintenance
- Electronic manuals and certificates
- Spares management and requisitioning
- Charter party, notice of readiness
Until recently, IT and OT systems were normally isolated from each other as well as from any external shore-based systems, but advancements in technology have allowed these two systems to integrate into one another.
When discussing cyber threats like these, it’s critical to consider the uniqueness of OT systems, since they control the physical world [source]. Challenges with OT systems to keep in mind include the following from Anastasios Arampatzis from Tripwire:
- They are responsible for real-time performance, and response to any incidents is time-critical to ensure the systems’ high reliability and availability.
- Access should be controlled strictly without altering the required human-machine interaction.
- Safety is extremely crucial because even the slightest downtime may not be acceptable.
- They have long life cycles. Any updates must be carefully designed and implemented (normally done by the vendor) to avoid disruption.
- They are designed to support an intended operational process. Due to this, they might not have enough memory and/or computing resources to support the addition of security capabilities.
Disruption to these systems can impose a significant risk to the safety and security of all on board the vessel and the cargo, as well as impede the ship’s operation and potentially could even damage the marine environment.
Chapter 3:
What is the Current Maritime Cyber Threat Landscape?
Moving in the path of digitizing shipping means there is a larger reliance on digital and communication systems, which leaves more space for a potential cyber safety incident.
According to “The Guidelines on Cybersecurity Onboard Ships, Version 3,” cybersecurity is concerned with the protection of IT, OT, information, and data from unauthorized access, manipulation, and disruption. Cybersafety covers the risks from the loss of availability or integrity of safety-critical data and OT. [source]
Recent events in the maritime industry have shown cyber threats are coming to fruition. In Sept. 2020, the French shipping company CMA CGM announced it had been hit by a ransomware attack. The “Ragnar Locker ransomware” attacked Chinese branches in Guangzhou, Shenzhen, and Shanghai and took down its worldwide shipping container booking system.
This recent attack marks a unique scenario because CMA CGM is now the 4th major shipping company to be hit by a cyber attack in the past four years.
In fact, according to ZDNet, “there is no other industry sector where the Big Four have suffered major cyber-attacks one after the other like this.”
Previous incidents with the “Big Four” since 2017 include:
APM-Maersk - taken down for multiple weeks by NotPetya ransomware in 2017
Mediterranean Shipping Company - attacked in April 2020 by an unnamed malware strain that brought its data center down for days.
COSCO - In July 2018, it was brought down for weeks due to ransomware.
While all four of these incidents are different, they do show that there is a targeting of the maritime shipping industry.
And the attacks don’t stop there.
Over the past year, incidents where malware landing on ships has grown, including sightings of USB malware, ransomware, and worms that have been found aboard a ship’s IT systems. [source]
"After Maersk was hit by the NotPetya crypter, I believe criminals realized the opportunity to bring a critical industry down, so payment of a ransom was perhaps more likely than other industries," said Ken Munro, a security researcher at Pen Test Partners
Attacks haven’t just been involved with targeting ships. In a statement on Thursday, Oct. 2, the International Maritime Organization (IMO) said it suffered “a sophisticated cyber attack against the organization’s IT systems.” [source] The attack caused a number of IMO web-based services to be unavailable and the breach also impacted its public website and internal systems.
Although it might be too soon to say whether the recent attacks will prove to be a brief annoyance or the start of wider damage, Bloomberg Intelligence’s Lee Klaskow says the cyber threats are a “near-term headwind and headache for sure.”
Recent Efforts to Inform and Protect Ship and Facility Owners
Source: Safety4Sea, YouTube “Unravelling the myth behind cybersecurity”
In March 2020, the US Coast Guard issued a new set of guidelines intended to assist facility owners and operators in complying with requirements to assess, document, and address various system and network risks.
These efforts by the US Coast Guard are to raise awareness of impending cyber threats that are growing in the maritime industry due to emerging technologies and digitization onboard vessels.
Last July, the US Coast Guard issued a safety alert that warned all shipping companies of maritime cyber-attacks. The actual incident that spawned this warning occurred back in February 2019 when a large ship on an international voyage headed for the Port of New York and New Jersey reported: “a significant cyber incident impacting their shipboard network.”
And this was not the only time a warning was released. In May 2019, the US Coast Guard published a bulletin to bring awareness to maritime stakeholders of possible malware and email phishing attacks targeting commercial vessels.
It’s no surprise that since over 90% of the world’s trade is transported by shipping, the maritime industry is an attractive target for cyber attackers, according to the United Nations’ International Maritime Organization (UNIMO).
The European Union (EU) has recognized the maritime industry’s importance and its impact on the global economy. They have included shipping in the Network and Informations Systems (NIS) Directive, an organization that deals directly with protection from cyber threats of national critical infrastructure. [source]
Chapter 4
6 Common Cyber Risks Affecting the Maritime Industry
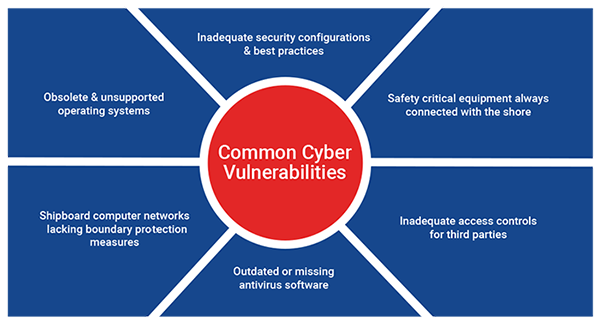
Source: Safety4Sea, https://safety4sea.com/cm-6-common-cyber-risks-affecting-maritime-industry/
Computer and cyber dependent technologies are crucial for vessel and facility operators because systems like communications, ballast, navigation, cargo, environmental control, and more all rely on the technology to be functioning at its best.
Emergency systems like security monitoring, fire detection, and alarms also heavily rely on cyber technology and can be targeted for a cyber attack. Because of these technologies and their importance on board a vessel, companies must plan for a cyberattack and check for any vulnerabilities on board or ashore.
Potential Cyber Risks Onboard
The following are common cyber vulnerabilities that can be found on board ships:
- Unsupported or obsolete operating systems
- Out of date or missing antivirus software and malware protection
- Inadequate security configurations and best practices
- Shipboard computer networks that might be lacking in boundary protection measures and segmentation of networks.
- Safety-critical equipment that’s always connected with the shore
- Inadequate access controls for third parties
While powerful, modern technologies can add vulnerabilities to a ship, especially if there is uncontrolled access to the Internet or insecure network designs. Another problem shipowners can run into is that onboard crew and onshore personnel might not be aware of the network system or how some equipment producers maintain remote access to shipboard equipment. [source]
That’s why it’s essential to consider the risks and build out a plan to address any vulnerabilities you may come across.
Chapter 5:
Best Practices to Mitigate Maritime Cybersecurity Risks (+ IMO Guidance)
The overarching goal of maritime cyber risk management is to support safe and secure shipping, which is operationally resilient to cyber risks.
The Baltic and International Maritime Council (BIMCO) developed “Guidelines on cybersecurity Onboard Ships,” closely aligning the aforementioned NIST Cybersecurity Framework.
Maritime companies should follow these best practices to reach the goal of operational resilience:
- Assess risk exposure by determining the likelihood and impact of vulnerability exploitation by any external or internal actor
- Identify the threat environment to understand external and internal cyber threats to the ship
- Identify vulnerabilities by developing full inventories of onboard systems and understanding the consequences of cyber threats to these systems
- Establish prioritized contingency plans to mitigate any potential identified cyber risk
- Develop protection and detection measures to reduce the likelihood and the impact of potential exploitation of a vulnerability
- Respond to and recover from cyber incidents using the contingency plan to ensure operational continuity
As discussed earlier in the article, the IMO recently published guidelines for maritime safety, and cyber risk management recommended to stakeholders.
The guidelines provide crucial steps to safeguard shipping from the current and emerging vulnerabilities and threats relating directly to digitization, integration, and automation of shipping processes and systems. [source]
Key recommendations from the IMO guidelines include:
- Effective cyber risk management should start at the senior management level.
- A risk-based approach should be adopted with a comprehensive assessment to compare an organization’s current and desired cyber risk management postures.
- The 5 Phases of the NIST Cybersecurity Framework should be considered as part of the response to the risk management review. These are also known as “Identify, Protect, Detect, Respond and Recover.”
- All operational systems should be included and the process and effectiveness reviewed regularly and a plan to communicate awareness throughout the organization should be implemented.
Senior management should embed a culture of cyber risk awareness into all levels of an organization and ensure a holistic and flexible cyber risk management regime in continuous operation and constantly evaluated through effective feedback mechanisms.
Such a comparison may reveal gaps that can be addressed to achieve risk management objectives through a prioritized cyber risk management plan.
The guidelines also identify specific systems that should be considered and monitored accordingly:
- Bridge systems
- Cargo handling and management systems
- Propulsion and machinery management and power control systems
- Access control systems
- Passenger servicing and management systems
- Passenger facing public networks
- Administrative and crew welfare systems
- Communication systems
In order to support these secure shipping initiatives, all companies and organizations that interact directly with the shipping industry should utilize these actionable guidelines and best practices to manage their cyber risk exposure.
Conclusion
Rapid technological developments have brought numerous benefits to our world and have improved many industries, including the world of shipping.
Increased access, connectivity, and networking of integrated OT and IT systems onboard ships have been an essential part of their operation and management and the safety and security of the crew, cargo, and the ship itself.
This digitization and connectivity to the Internet, while it has brought many benefits, also increases the risk of cybersecurity threats and attacks, as we’ve outlined above.
By following the various guidelines from the US Coast Guard, IMO as well as the best practices from BIMCO, shipping companies can take action to ensure their assets are protected and operationally resilient to cyber risks.
If you are looking for a quality, premier coatings solutions provider to help you with the physical protection of your assets, we can help. Our value-added marine coatings can handle the widest range of chemicals used in transport, has superior chemical resistance and product purity, cleans easily, and is a proven performer in the maritime market.






